IAM KeyCloak
Зачем
Реализация функции Identity and Access Management (IAM) решений.
Функции
- Custom UI forms Apache Freemaker + React?
- ReCaptcha v3 Google
- Flow-Grants
- Tokens
- Custom Fields Token
- Refresh token rotation
- Revoke Refresh Token
- Token Expiration
- Шифрование JSON Web Encryption (JWE) RSA
- only support ID Token
- JSON Web Key (JWK) – это структура данных в формате JSON, представляющая криптографический ключ.
- JWT RSA algorithm
- RSA_OAEP_256 - RSAES using Optimal Asymmetric Encryption Padding (OAEP) (RFC 3447), with the SHA-256 hash function and the MGF1 with SHA-256 mask generation function.
- RSA_OAEP - DEPRECATED - RSAES using Optimal Asymmetric Encryption Padding (OAEP) (RFC 3447), with the default parameters specified by RFC 3447 in section A.2.1. Use of this encryption algorithm is no longer recommended, use RSA_OAEP_256 instead.
- Template Email
- REST API
- Управление пользователями
- REST API Postman Collection
- Custom Extension Plugin
- 2FA
- HMAC based OTP (HOTP)
- Time based OTP (TOTP)
- ЕСИА
- 2FA SMS
- User Store\Provider
- User Federation (Sync) - password not import, keycloak delegate
- AD, LDAP, Kerberos
- DB sync, PSQL with password
- API
- REST SPI user-storage Custom User provider
- REST API System for Cross-domain Identity Management (SCIM)
- SCIM Client - IDP Keycloak
- SCIM 1.0 Provisioning SPI
- SCIM 2.0 GNU Affero General Public License v3.0
- SCIM Client - IDP Keycloak
- On demand migration
- External Identity broker OIDC
- User Federation (Sync) - password not import, keycloak delegate
- Message Queue Intgegration
- Keycloak SPI plugin that publishes events to a RabbitMq server
- Keycloak SPI plugin Kafka
- Keycloak v19 sending logs using GELF to centralized logging solutions like ELK, EFK or Graylog out of the box.
- Session State
- обмен cookie через iframe механизм не все браузеры будут поддерживать в дальнейшем
- JavaScript Adapter for Client App
Термины
- Realm - необходимо ограничение по кол-ву, риски по НТ
- Users входят в Realm
- Clients входят в Realm
- MTA подход можно реализовать
- Groups
- Roles
- Cross-Origin Resource Sharing (CORS)
- CORS allow using the Authorization Code flow in JavaScript on browser-side with the PKCE extension instead.
Обновление Access Token используя Refresh Token
Параметры KeyCloak
-
Максимальное время жизни Access токена, сек “accessTokenLifespan” - 10800с=3ч (5мин) 60 -
Максимальное время жизни access токена для Implicit Flow, сек “accessTokenLifespanForImplicitFlow” - 10800 60 -
Если пользователь неактивен дольше указанного времени, то сессия истекает., сек Касается Refresh токенов, и браузеров. “ssoSessionIdleTimeout” - 2592000с=30д 120 - Можно продлить сессию через Refresh Token
-
Максимальное время жизни сессии, после чего сессия истекает. Касается Refresh токенов, и браузеров, сек. “ssoSessionMaxLifespan”: 15552000=180д 180 - Нельзя продлить сессию используя Refresh Token
- То же самое, что SSO Session Idle, но для Refresh токена. Если на задано, то используется “ssoSessionIdleTimeout” “clientSessionIdleTimeout” - 0
- То же самое, что SSO Session Max, но для Refresh токена. Если на задано, то используется “ssoSessionMaxLifespan” “clientSessionMaxLifespan” - 0
- То же самое, что SSO Session Idle, но при нажатом “Запомнить меня” “ssoSessionIdleTimeoutRememberMe” - 0
- То же самое, что SSO Session Max, но при нажатом “Запомнить меня” “ssoSessionMaxLifespanRememberMe” - 0
User Storage
User Federation
- REST SPI Custom User provider реализация интерфейсов org.keycloak.storage.UserStorageProviderFactory - Allows Keycloak to access custom user stores.
Access Control
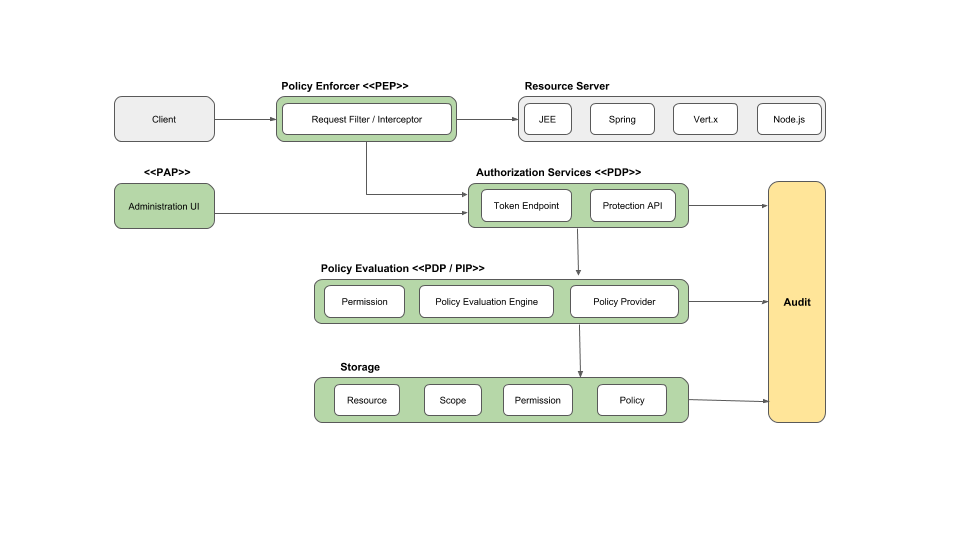
- Policy Administration Point (PAP)
- Policy Decision Point (PDP)
- Policy Enforcement Point (PEP)
- Policy Information Point (PIP)
Термины:
- resource - метод API, например
- scopes - usually indicates what can be done with a given resource. Example of scopes are view, edit, delete, and so on.

- permission - X CAN DO Y ON RESOURCE Z
- protect resource or scope
- policy

- Policy provider custom
Проверка через Policy Evaluation Tool
Управление resource, scopes, permission, policy:
User-Managed Access (UMA) 2.0. UMA is a specification that enhances OAuth2 capabilities in the following ways:
- Privacy - Nowadays, user privacy is becoming a huge concern, as more and more data and devices are available and connected to the cloud. With UMA and Keycloak, resource servers can enhance their capabilities in order to improve how their resources are protected in respect to user privacy where permissions are granted based on policies defined by the user.
- Party-to-Party Authorization - Resource owners (e.g.: regular end-users) can manage access to their resources and authorize other parties (e.g: regular end-users) to access these resources. This is different than OAuth2 where consent is given to a client application acting on behalf of a user, with UMA resource owners are allowed to consent access to other users, in a completely asynchronous manner.
- Resource Sharing - Resource owners are allowed to manage permissions to their resources and decide who can access a particular resource and how. Keycloak can then act as a sharing management service from which resource owners can manage their resources.
Example
- RBAC
- ответственность за менеджмент ролей перекладываем из Keycloak на этот кастомный продукт. Затем при взаимодействии сервисов друг с другом они обращаются в этот permission-сервис и получают тот или иной набор разрешений. А уже на стороне сервиса валидируется, может ли пользователь в соответствии с разрешением выполнять операцию.
Технологии
- Java
- PostgreSQL
- k8s
- GoGatekeeper
Deployment
- CPU RAM
- Минимальные системные требования под keycloak (под 19ю версию не нашел).
- Требуемые ресурсы CPU RAM уточнить по итогу Benchmarks keycloak под НФТ.
- HA
- k8s
- Режим разворачивания в ПРОДе в отказоустойчивом (HA) кластере на СУБД postgresql с распределенным кешем Infinispan, вариант «Обычный кластер»
- docker
- https TLS 1.3
Observability
- Метрики мониторинга производительности
- health check
- logs
Metric
- keycloak_response_errors
- keycloak_login_attempts
- keycloak_failed_login_attempts
- keycloak_failed_client_login_attempts
- keycloak_refresh_tokens